The team says their framework can scalably and semi-automatically monitor the use of filtering technologies for censorship at global scale.
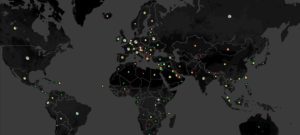

The team says their framework can scalably and semi-automatically monitor the use of filtering technologies for censorship at global scale.
Researchers carried out the first study on voter behavior with electronic assistive devices, found 93% missed incorrect ballots.
The post Not enough voters detecting ballot errors and potential hacks, study finds appeared first on Michigan Engineering News.
The proposal provides a chip-level safeguard against sensitive data being transmitted after it’s accessed.
A Q&A with J. Alex Halderman, who co-founded the nonprofit organization.
The post How Let’s Encrypt doubled the percentage of secure websites in four years appeared first on Michigan Engineering News.
The nation is using inexpensive commodity equipment to block 170K domains on more than 1K privately-owned ISPs.
The post How Russia’s online censorship could jeopardize internet freedom worldwide appeared first on Michigan Engineering News.

The newly discovered microphone vulnerability allows attackers to remotely inject inaudible and invisible commands into voice assistants using light.
The new system is designed to save security researchers time and effort spent reverse-engineering the message format of every vehicle they study.

Technology pioneered by Michigan researchers can circumvent many effective website blocking tools

All three of these attacks put users’ privacy at risk, exploiting new routes to sensitive data.
The researchers demonstrated that an adversary could remotely manipulate the temperature sensor measurements without tampering with the targeted system or triggering automatic temperature alarms.