Cybersecurity
Are autonomous vehicles so great if your car gets hacked?
What if someone took control of a city’s traffic signals or water treatment? With reliance on remote sensing and control algorithms, how can someone be sure they aren’t falling prey to faked data when making decisions? Think about what’s needed to protect against interference with the electronic and human systems embedded in every process.
Explore all
You’re just a stick figure to this camera
The anonymity could reduce unnecessary surveillance in an age of smart devices.
The post You’re just a stick figure to this camera appeared first on Michigan Engineering News.
Managing screen time by making phones slightly more annoying to use
Delaying a phone’s swiping and tapping functions forces users to think harder, making it easier for them to consider whether to keep scrolling.
The post Managing screen time by making phones slightly more annoying to use appeared first on Michigan Engineering News.
Blue PHOLEDs: Final color of efficient OLEDs finally viable in lighting
Synchronizing light and matter adds blue to the OLED color palette
The post Blue PHOLEDs: Final color of efficient OLEDs finally viable in lighting appeared first on Michigan Engineering News.
Automotive semiconductor effort builds momentum
‘The innovation needs of the auto industry present a new set of opportunities for the semiconductor community.’
The post Automotive semiconductor effort builds momentum appeared first on Michigan Engineering News.

Thatchaphol Saranurak recognized with 2023 Presburger Award
The award recognizes the outstanding contributions of a young scientist in the field of theoretical computer science.
New apps for visually impaired users provide virtual labels for controls and a way to explore images
With VizLens, users can touch buttons while their phones read out the labels, and Image Explorer provides a workaround for bad or missing alt text.
The post New apps for visually impaired users provide virtual labels for controls and a way to explore images appeared first on Michigan Engineering News.
New kind of transistor could shrink communications devices on smartphones
Integrating a new ferroelectric semiconductor, it paves the way for single amplifiers that can do the work of multiple conventional amplifiers, among other possibilities.
The post New kind of transistor could shrink communications devices on smartphones appeared first on Michigan Engineering News.

Andrew Wintenberg awarded Predoctoral Fellowship to support research impacting the safety of smart systems
Wintenberg is developing computer algorithms and tools to improve the security of cyber and cyber-physical systems.
Nanoscale ferroelectric semiconductor could power AI and post-Moore’s Law computing on a phone
Next-gen computing material gets down to the right size for modern manufacturing.
The post Nanoscale ferroelectric semiconductor could power AI and post-Moore’s Law computing on a phone appeared first on Michigan Engineering News.
Scalable method to manufacture thin film transistors achieves ultra-clean interface for high performance, low-voltage device operation
Led by Prof. Becky Peterson, the research focuses on a category of materials important for low power logic operations, high pixel density screens, touch screens, and haptic displays.
The post Scalable method to manufacture thin film transistors achieves ultra-clean interface for high performance, low-voltage device operation appeared first on Michigan Engineering News.

Six ECE faculty will help shape the future of semiconductors as part of the JUMP 2.0 program
Elaheh Ahmadi, David Blaauw, Michael Flynn, Hun-Seok Kim, Hessam Mahdavifar, and Zhengya Zhang bring their expertise and creativity to this nationwide undertaking in the area of semiconductors and information & communication technologies.
Open-source hardware: a growing movement to democratize IC design
Dr. Mehdi Saligane, a leader in the open-source chip design community, was among the first researchers to fabricate a successful chip as part of Google’s multi-project wafer program.
The post Open-source hardware: a growing movement to democratize IC design appeared first on Michigan Engineering News.

Major breakthrough in dynamic graph algorithms earns Best Paper
Thatchaphol Saranurak and collaborators were recognized at SODA ’23 for their work that broke an approximation barrier in dynamic graph matching.
Cyber vulnerability in networks used by spacecraft, aircraft and energy generation systems
A new attack discovered by the University of Michigan and NASA exploits a trusted network technology to create unexpected and potentially catastrophic behavior
The post Cyber vulnerability in networks used by spacecraft, aircraft and energy generation systems appeared first on Michigan Engineering News.
Expert: 4 ways Americans can keep their vote secure and accurate
With election security experts waylaid by years debunking false claims of election fraud, little has improved since 2020.
The post Expert: 4 ways Americans can keep their vote secure and accurate appeared first on Michigan Engineering News.

Can sound be used as a weapon? 4 questions answered
What happened to people inside the U.S. Embassy in Havana?

Michigan researchers discover vulnerabilities in next-generation connected vehicle technology
The vulnerability allows an attacker to manipulate a new intelligent traffic control algorithm and cause severe traffic jams.

Building a security standard for a post-quantum future
A large quantum computer could retroactively decrypt almost all internet communication ever recorded.

Undocumented immigrants’ privacy at risk online, on phones
When it comes to their smartphones, immigrants struggle to apply instinctive caution, according to a study by a team of University of Michigan researchers.

Tyche: A new permission model to defend against smart home hacks
“The work is an important step towards understanding how to make tradeoffs between usability and security.”

A secure future for US elections starts in the classroom
A new special topics course on election cybersecurity gives students an examination of the past, present, and future of US elections.
Study reveals new data on region-specific website blocking practices
A team of researchers unearthed new data on geographic denial of access to web content in a new paper.

Facebook Fellowship for research on web privacy, security, and censorship
McDonald works to develop better privacy and security tools for marginalized communities

Election security: Halderman recommends actions to ensure integrity of US systems
In congressional testimony, professor urges $370M in federal funding to replace outdated machines.
Halderman co-chairs new commission to protect Michigan votes
The effort seeks to protect the integrity of every vote.

Michigan’s new Election Security Commission holds inaugural meeting on U-M Campus
The meeting began the commission’s review and assessment of election security in Michigan.

Best paper award for analysis of a decade of malware reports
The research suggests that common blacklist-based prevention systems are ineffective.

PET Award for making privacy policies easier to read
The research generated a chatbot to help users sift through important details in privacy policies.
Remote attack on temperature sensors threatens safety in incubators and industry
The researchers demonstrated that an adversary could remotely manipulate the temperature sensor measurements without tampering with the targeted system or triggering automatic temperature alarms.

Year of vulnerability hunting uncovers potential attacks on Intel Chips, RAM
All three of these attacks put users’ privacy at risk, exploiting new routes to sensitive data.

New tool combats evolving internet censorship methods
Technology pioneered by Michigan researchers can circumvent many effective website blocking tools
Offensive vehicle security toolbox makes car hacking easier
The new system is designed to save security researchers time and effort spent reverse-engineering the message format of every vehicle they study.

Researchers take control of Siri, Alexa, and Google Home with lasers
The newly discovered microphone vulnerability allows attackers to remotely inject inaudible and invisible commands into voice assistants using light.
Researchers design new solution to widespread side-channel attacks
The proposal provides a chip-level safeguard against sensitive data being transmitted after it’s accessed.
Real-time monitor tracks the growing use of network filters for censorship
The team says their framework can scalably and semi-automatically monitor the use of filtering technologies for censorship at global scale.

Todd Austin Named S. Jack Hu Collegiate Professor of Computer Science and Engineering
Prof. Austin is a creative, outside-the-box thinker who has produced a body of work that has had extraordinary impact in the area of computer architecture.

IEEE security conference features six accepted papers from CSE researchers
The projects impact voting systems, physical sensors, integrated circuit fabrication, and multiple microarchitectural side-channel vulnerabilities.

New collaboration promises greater innovation in medical device security
The two organizations will connect their membership and partner networks to work on advancing security for life-saving devices.

CSE researchers help organize 10th anniversary workshop on internet freedom
Prof. Roya Ensafi and PhD candidate Reethika Ramesh led organizing efforts for USENIX’s Tenth Workshop on Free and Open Communications on the Internet.

Censored Planet: Tracking internet censorship without on-the-ground participation
Censored Planet is releasing technical details for other researchers and for activists.

Major side-channel discovery wins NSA contest
The winning paper broke open a new area of investigation in hardware-based data leaks.
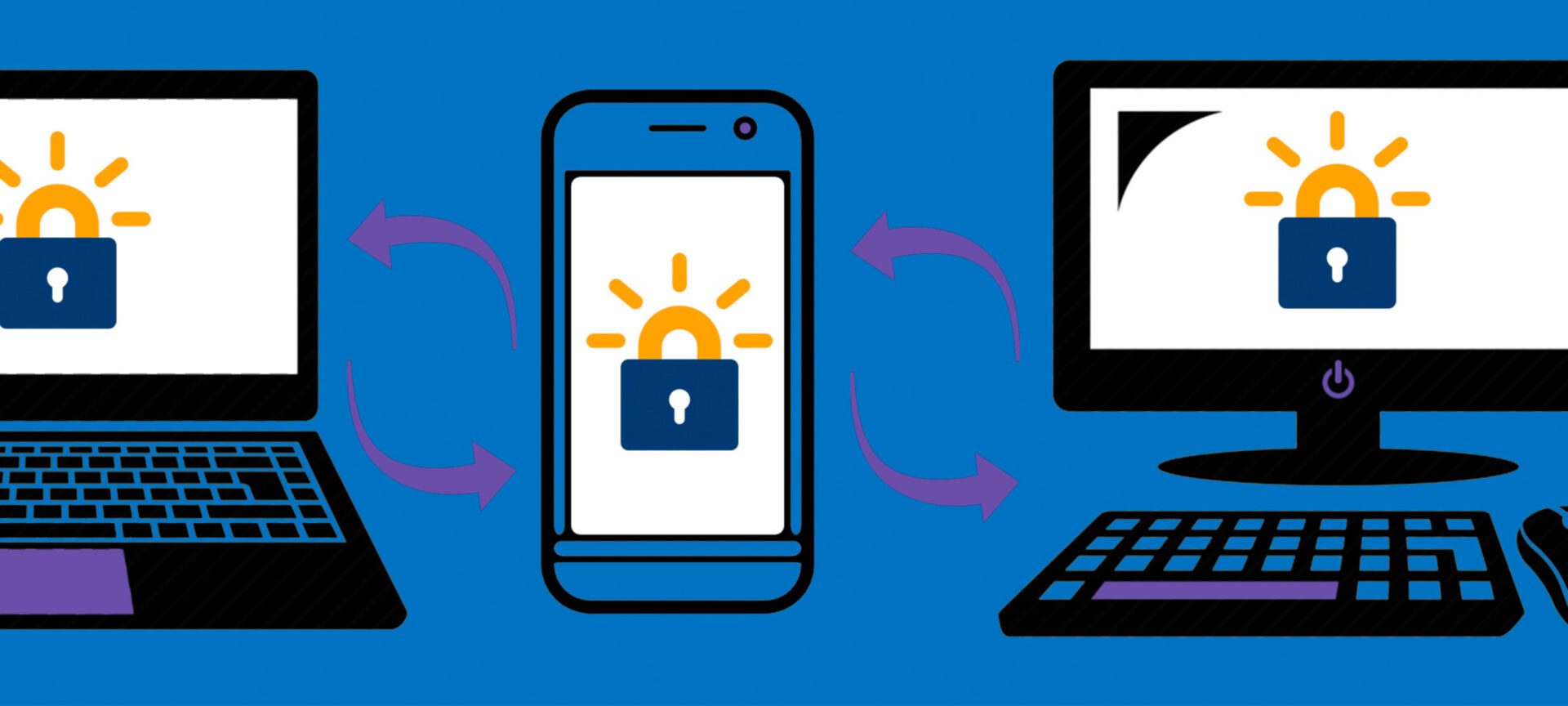
After five years, Let’s Encrypt, a non-profit based on tech developed at Michigan, has helped to secure the internet
Today, over 225 million websites are protected by free certificates issued by Let’s Encrypt.

Hacking reality
Microphones that “hear” light; microprocessors that “tell” us secrets; self-driving cars that “see” fake objects; sensors that “feel” the wrong temperature. Our devices are under attack in new, increasingly sophisticated ways. Security researchers at CSE are exploring the limits of hardware and finding new, sobering vulnerabilities in our computers and homes.

Five ways to keep vaccine cold storage equipment safe from hackers
A medical security expert outlines the risks and how hospitals can protect themselves.

U-M spin-off Agita Labs releases always encrypted computing product
TrustForge, based on U-M research spearheaded by Austin and Bertacco, provides users with the ability to protect data using a process called sequestered encryption

U-M and AT&T researchers develop energy efficiency profiling technology for mobile platforms

Sneak attack through smartphone shared memory
A weakness believed to exist in Android, Windows and iOS operating systems could be used to obtain personal information from unsuspecting users, research at the University of Michigan has shown.
$3.46M to Combine Machine Learning on Big Data with Physical Simulations
The focal point of the project will be a new computing resource, called ConFlux, which is designed to enable supercomputer simulations to interface with large datasets while running.
Secure your website now: Let’s Encrypt enters Public Beta
Let’s Encrypt allows anyone to request a free website security certificate without needing an invitation.

Mosharaf Chowdhury receives Google Faculty Research Award
The project aims to create a new software stack for analytics over geo-distributed datasets.
GridWatch named finalist in Vodafone’s eighth annual Wireless Innovation competition
GridWatch can detect power outages by monitoring changes to its own power state, locally verifying these outages using a variety of sensors that reduce the likelihood of false power outage reports, and corroborating actual reports with other phones through data aggregation in the cloud.

Thorny technical questions remain for net neutrality
Not all online traffic is the same; should we treat it the same anyway?

Proxy optimizes webpage loading for better user experience
Klotski seeks to improve users’ perceptions of how quickly a page loads by maximizing the amount of important content on the page that is fetched and displayed within the user’s attention span.

Tracking and mitigating tail latency in data centers
High tail latency has been identified as one of the key challenges facing modern data center design.
Several Michigan Papers Presented at 2016 USENIX Security Symposium
A total of five papers authored by CSE researchers were presented.
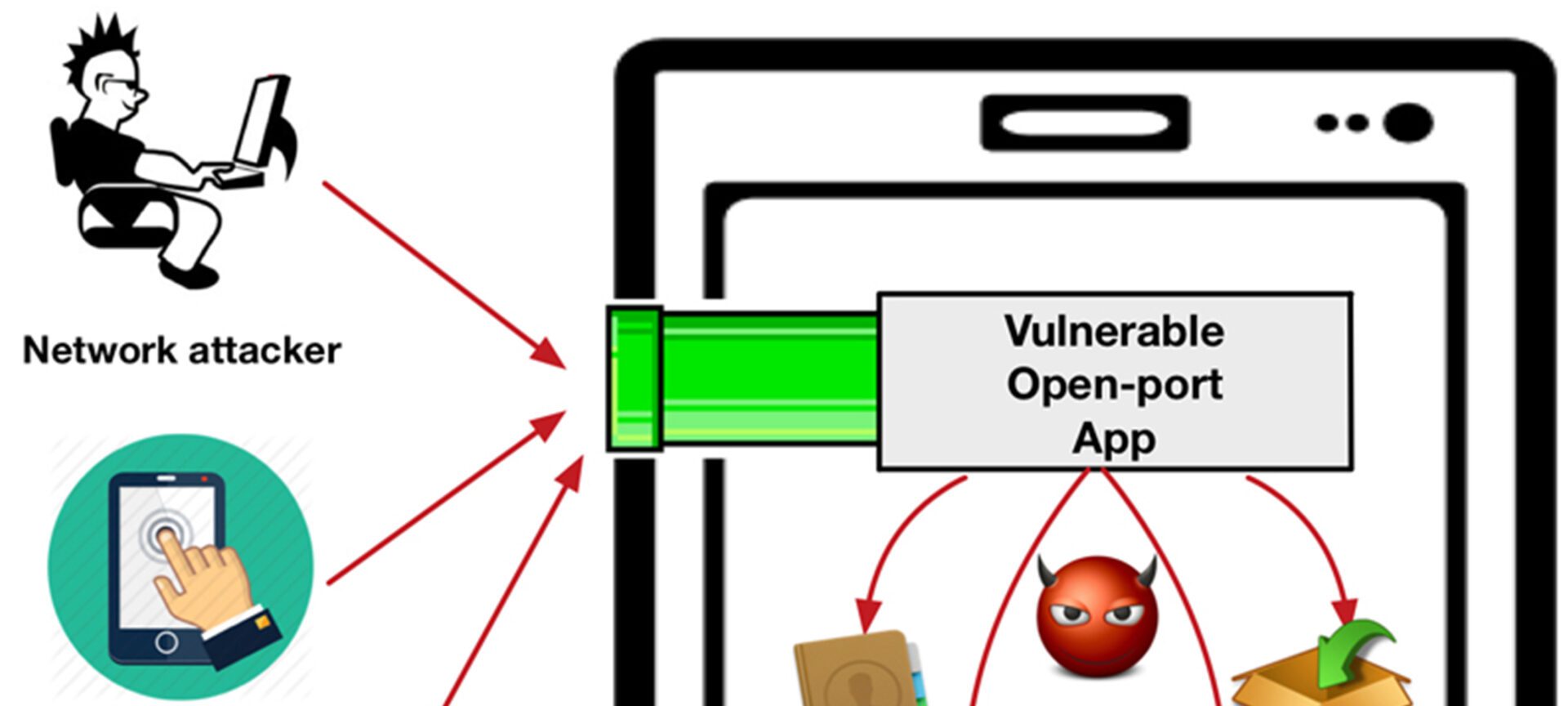
Open ports act as security wormholes into mobile devices
Researchers have for the first time characterized a widespread vulnerability in the software that runs on mobile devices.

Net neutrality repeal: Michigan Engineers weigh in
On Dec. 14, the FCC will vote on the rules that today ensure internet service providers treat all web content equally.
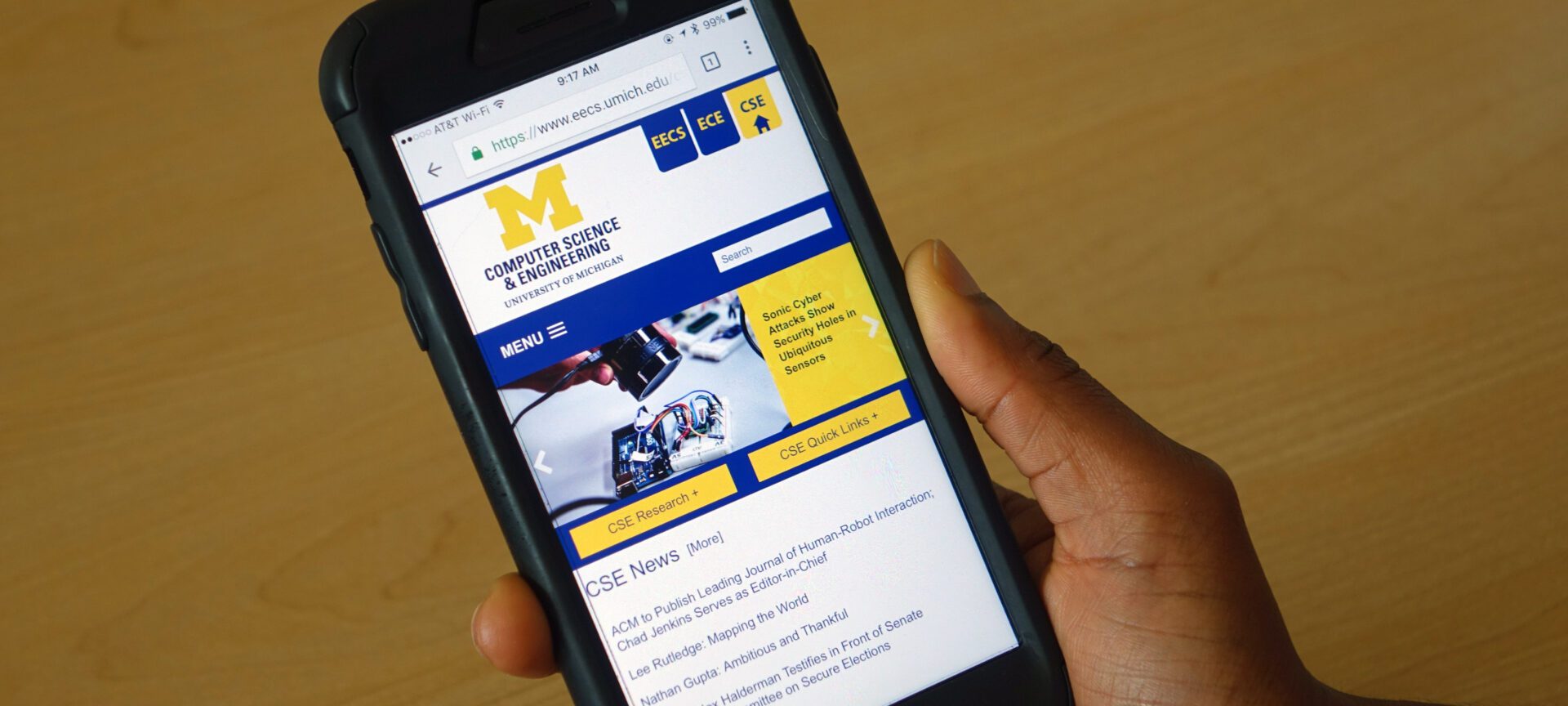
Michigan researchers awarded 2018 Applied Networking Research Prize for their work on speeding up the mobile web
The researchers, including Prof. Harsha Madhyastha and CSE graduate students Vaspol Ruamviboonsuk and Muhammed Uluyol, received prize for their paper, “Vroom: Accelerating the Mobile Web with Server-Aided Dependency Resolution.”

Designing a flexible future for massive data centers
A new approach recreates the power of a large server by linking up and pooling the resources of smaller computers with fast networking technology.
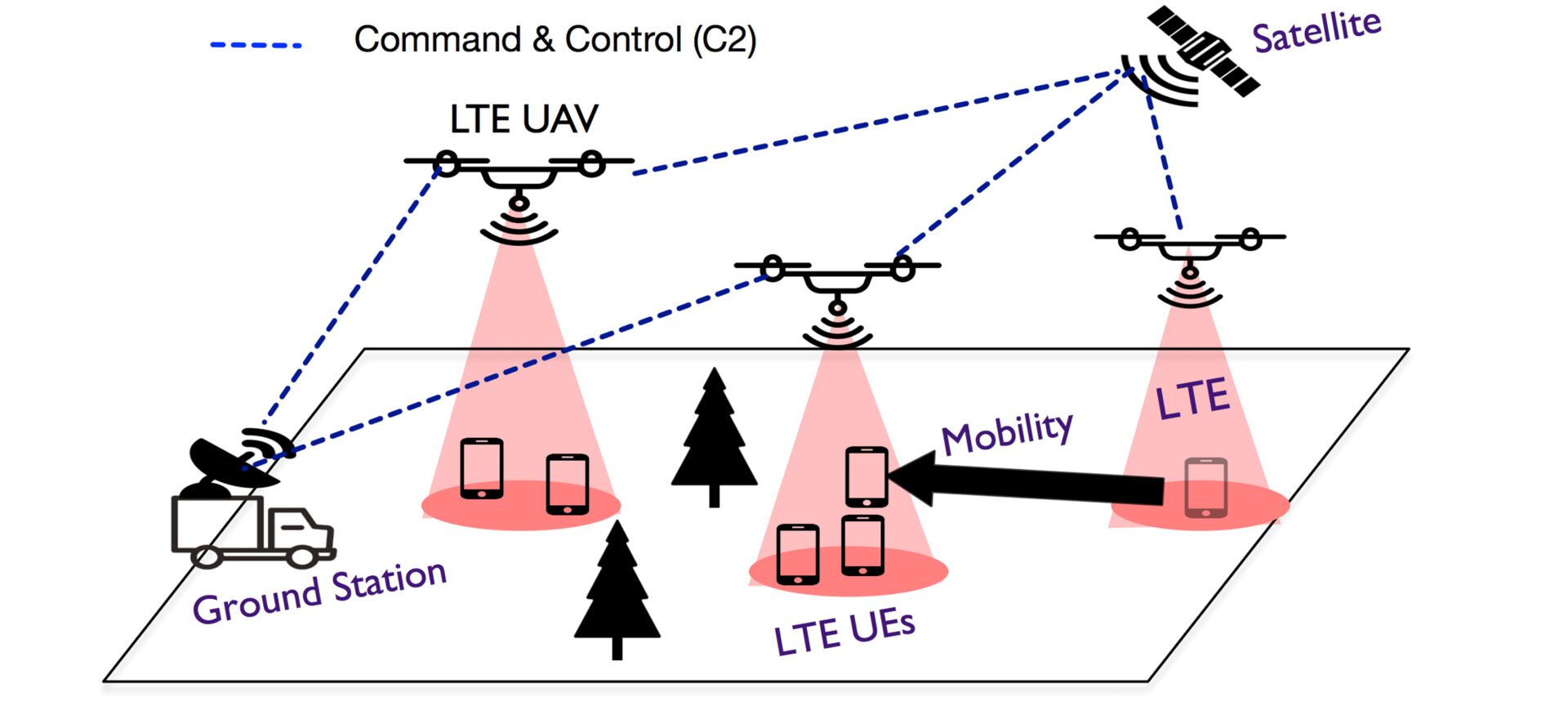
Using drones, a new software tool can bring LTE networks anywhere
SkyCore is a complete software solution to deploying mobile networks on unmanned drones
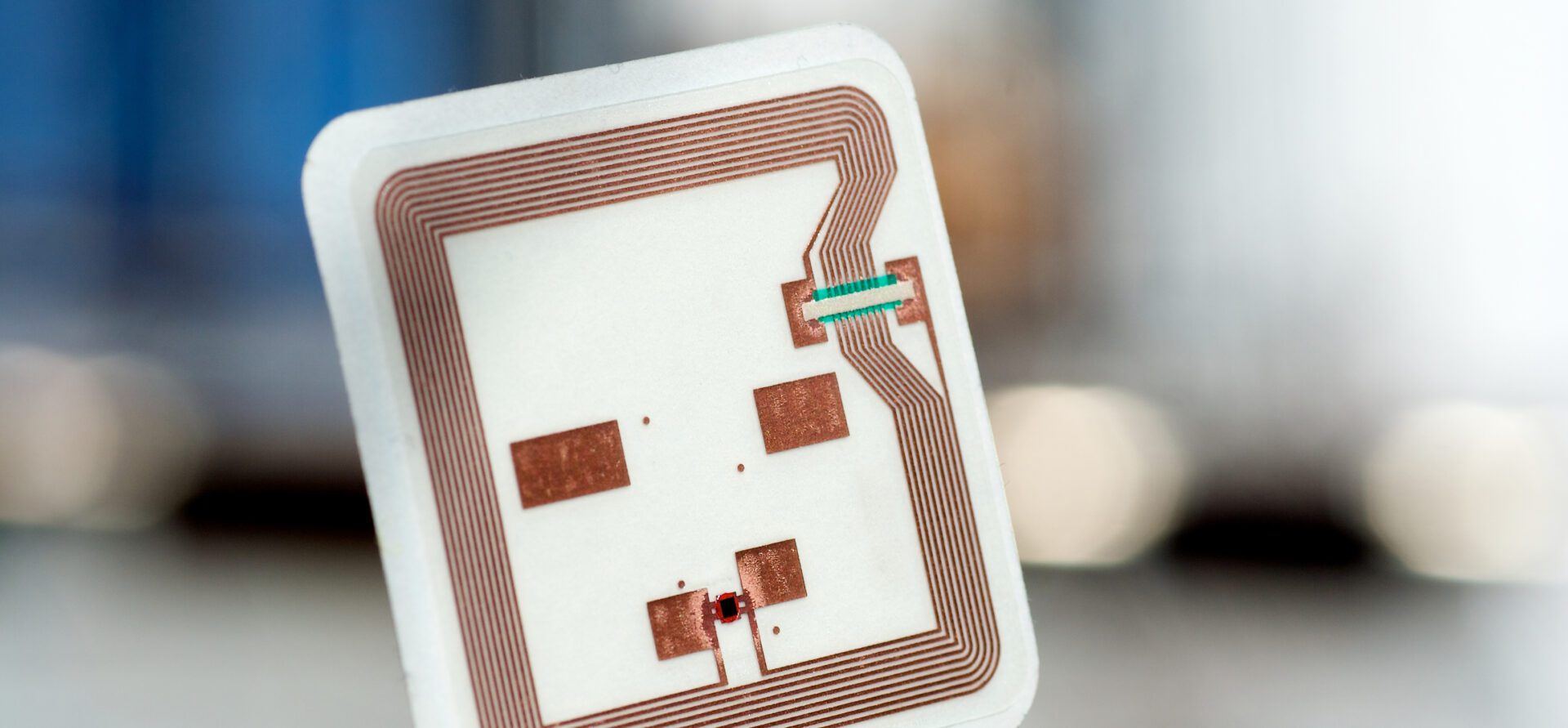
All things can be part of the Internet of Things with new RFID system
Sensing technology could keep seniors safe.

Army Award to speed up distributed methods over networks
Danai Koutra has earned an Army Young Investigator Award to speed up graph methods for distributed applications.

Chowdhury receives VMWare Award to further research on cluster-wide memory efficiency
Chowdhury’s work has produced important results that can make memory in data centers both cheaper and more efficient.

Award for helping popular websites better direct their internet traffic
Edge Fabric offers providers real-time performance analysis and a way to incorporate this data into routing decisions.

Facebook Fellowship for improving high-demand web services
Akshitha Sriraman works to enable hyperscale computing on high-demand web services.

$1M grant to develop U-M high-capacity research network
The team will develop a secure, data-intensive network solution to effectively transport extremely high volumes of research data on and off campus.

Five papers by CSE researchers presented at NSDI
The teams designed systems for faster and more efficient distributed and large-scale computing.

Enabling fairer data clusters for machine learning
Their findings reduce average job completion time by up to 95% when the system load is high, while treating every job fairly.

“Hiding” network latency for fast memory in data centers
A new system called Leap earned a Best Paper award at USENIX ATC ‘20 for producing remote memory access speed on par with local machines over data center networks.

Enabling efficient, globally distributed machine learning
A group of researchers at U-M is working on the full big data stack for training machine learning models on millions of devices worldwide.

Z. Morley Mao elected IEEE fellow for contributions to performance and security of internet routing and mobile systems
Prof. Mao and her students have played an important role in understanding the efficiency, security, and performance of a number of mobile systems.

Bringing smart banking to market
Jason Mars, CEO of Ann Arbor startup Clinc, was named #2 in Bank Innovations’s “10 Most innovative CEOs in Banking 2017” list. Clinc is leading the pack for development of intelligent banking assistant software.
“Stitching” together a web user from scattered, messy data
Even though we interact with different web services in different ways, there are clues in the data that can indicate trends and identify a unique profile.

Study maps careers of CS PhDs using decades of data
The researchers identified movement between industry, academia, and government work, tracked the growth of important organizations, and built predictive models for career transitions and employer retention.
Finding meaning in varied data
Jie Song devised a method to combine summarized datasets that group information by incompatible units.

Tool for structuring data creates efficiency for data scientists
Foofah is a tool that can help to minimize the effort and required background knowledge needed to clean up data.

Making software failures a little less catastrophic
Researchers have implemented a new way to diagnose software failures with a high degree of accuracy and efficiency.
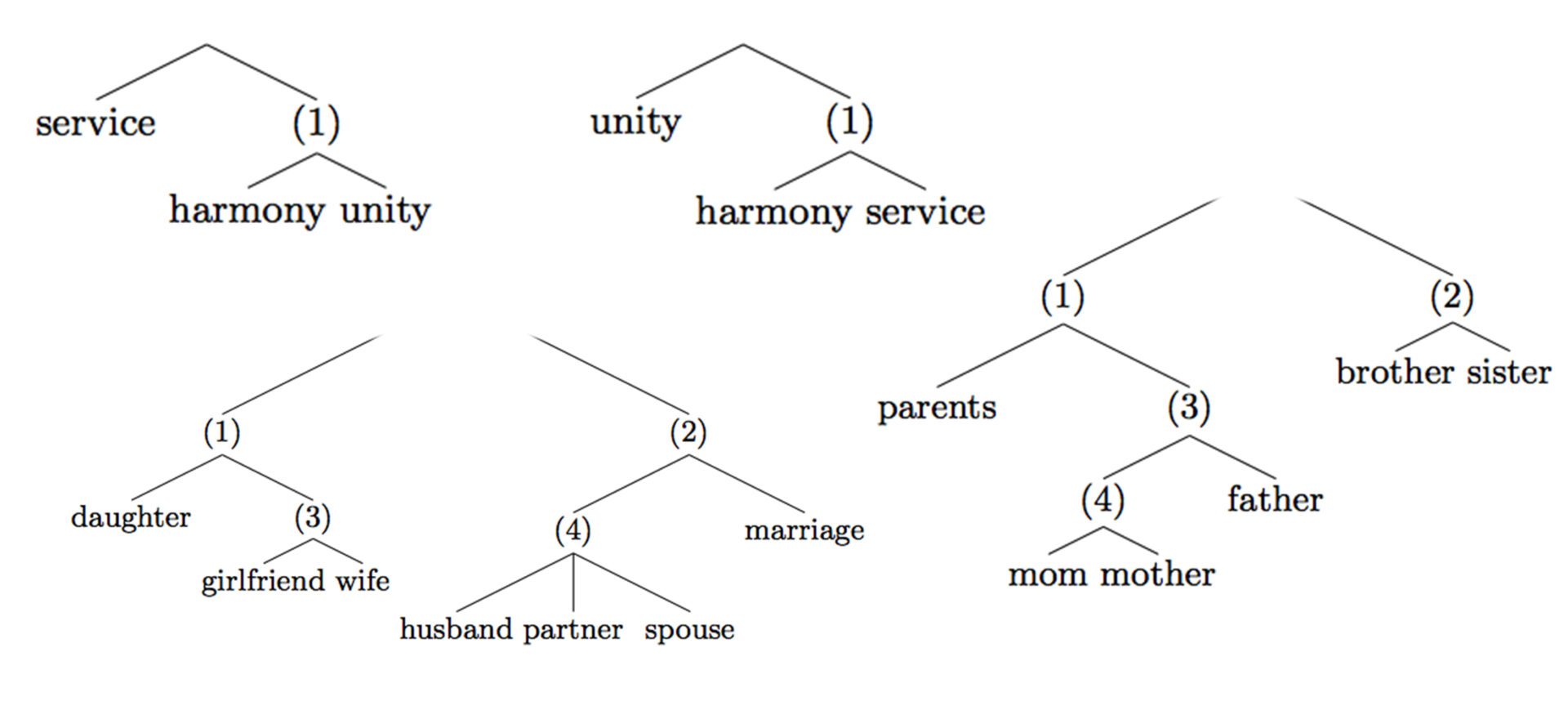
Gaining a deeper understanding of how personal values are expressed in text
Researchers used hierarchical trees to provide a better idea of how concepts are represented and related in a collection of text.

Helping drivers use smart cars smarter
This conversational in-vehicle digital assistant can respond to drivers’ questions and commands in natural language

Speeding up code with clever data manipulation
Kasikci presents a method to improve a program’s ability to use data in a straightforward, efficient way

Personalized knowledge graphs for faster search and digital assistants
Graphs that are customized, stored locally, and able to change over time can enable faster and more accurate searching and digital assistants

Two solutions for GPU efficiency can boost AI performance
Chowdhury’s lab multiplied the number of jobs a GPU cluster can finish in a set amount of time

Paper award for identifying speaker characteristics in text messages
The goal of the work was to identify seven things about who the subject was talking to just by analyzing text messages.

Student awarded NSF Fellowship for automating speech-based disease classification
Perez’s research focuses on analyzing speech patterns of patients with Huntington Disease.

CAREER Award for deeper insights into interconnected data: from neurons to web searches
Danai Koutra earned the award for her proposal to innovate the way we use networks to understand the world and speed up our technology.

Automated tool optimizes complex programs better than humans
Erie provided database repairs that were previously performed exclusively by human programmers.

“Mind reading” study looks inside coders’ brains
Using real-time fMRI readings, researchers linked spatial reasoning with CS problem solving.
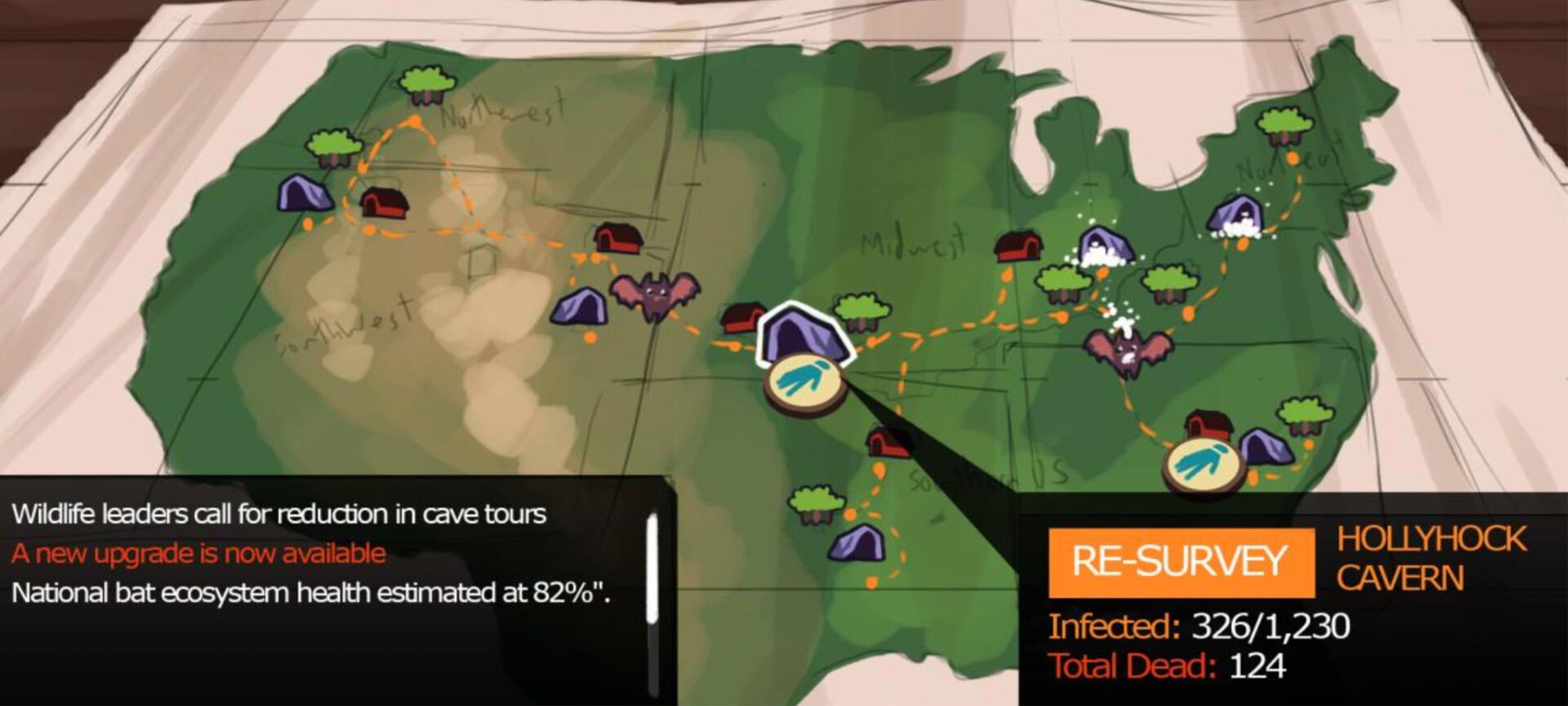
New browser strategy game has players tackle real-life bat catastrophe
As a fungal infection ravages bat populations, the new game hopes to promote public awareness of ongoing research to combat the issue.

Creating more efficient data centers for AI
Tang’s project will redesign data center systems to support large-scale use of hardware accelerators to meet future computational demand.
$1M NSF grant supports new system for gathering, structuring data with ease
The team’s new tool will combine of software and data to make gathering structured data dramatically easier.
$2M NSF grant to explore data equity systems
Researchers plan to establish a framework for a national institute that would enable research using sensitive data, while preventing misuse and misinterpretation.

CSE faculty bring significant showing to major systems conference
Researchers designed three new systems to speed up code at several key bottlenecks.

Best Student Paper Award for work on faster network classification for machine learning
Comparing graphs the team’s tool is up to an order of magnitude faster than competitive baselines.

Three faculty earn MIDAS grants to broaden the frontiers of data science
This round of funding strongly encourages pioneering work with the potential for major expansion.

Generating realistic stock market data for deeper financial research
A team at Michigan proposed an approach to generating realistic and high-fidelity stock market data to enable broader study of financial markets.
Emotion recognition has a privacy problem – here’s how to fix it
Researchers have demonstrated the ability to “unlearn” sensitive identifying data from audio used to train machine learning models.
Programming around Moore’s Law with automatic code translation
Most programs in use today have to be completely rewritten at a very low level to reap the benefits of hardware acceleration. This system demonstrates how to make that translation automatic.

Predoctoral Fellowship for mathematically provable hardware design
Goel designs algorithms that can automatically demonstrate the correctness of hardware systems.

Rackham Predoctoral Fellowship for design of robust, reliable and repairable software systems
Subarno Banerjee uses program analysis to improve software systems’ safety and security.
Undergraduate research on speeding up data centers earns ACM first prize
The student’s project targets critical moments where the next instruction in a program is only available in a slower type of memory.

Building better coronavirus databases with automatic quality checks
The team will build high-quality datasets to enable automatic quality checking and fraud detection of the new coronavirus data.

Research team takes on food insecurity in Detroit in the face of coronavirus limitations
Researchers are working with the city on two key initiatives to address food availability for elderly and low-income populations.

Get to know: Xinyu Wang
“My research has the potential to democratize programming and make it possible for millions of people around the globe to automate otherwise tedious tasks using programming.”

New method ensures complex programs are bug-free without testing
The system targets software that runs using concurrent execution, a widespread method for boosting performance, and proves whether a program will output what it’s supposed to.

NIST finalists for post-quantum security standards include research results developed by Prof. Chris Peikert
A new secure code is needed to protect private information from the power of quantum computing.
Alumnus Yi-Jun Chang Wins PODC Dissertation Award
His work is in complexity theory of distributed computing.

Prof. Baris Kasikci recognized as rising star by Intel
The award recognizes early career faculty who show great promise in developing future computing technologies.

Tool to automate popular security technique earns distinguished paper
The new technique automatically constructs policies for applications that keep them from compromising other programs.

Building a testing-free future
How automated guarantees that our most complex programs are secure and trustworthy can save us time, money, and anxiety.

New database sheds light on Michigan’s videogame boom
The Michigan Game Studios database, developed by lecturer Austin Yarger, helps organize the state’s rapidly growing scene.

Tim Dunn selected for NSF Graduate Research Fellowship
Through his work, Tim hopes to dramatically accelerate genomic sequencing analysis, enabling the use of handheld genomic sequencers to produce actionable diagnostic data within minutes.

Postdoc Leqi Zhu wins PODC Dissertation Award
The thesis completely solves a longstanding open problem in the theory of distributed computing.

Solution for restoring faulty graphs earns best paper award
Prof. Greg Bodwin has devised a solution to an important open question in graph theory that offers promising new options for repairing and constructing resilient networks.

Google Award to make widely used software testing technique more effective
Baris Kasikci plans to improve software fuzzers by learning how deployed software is most commonly run by users.

Using negative probability for quantum solutions
Probabilities with a negative sign have been of great use in quantum physics.

Censys enables fast searching of actionable internet data
The software enables users to ask questions about the hosts and networks that compose the Internet and get an immediate reply.

Barzan Mozafari receives NSF CAREER Award to improve predictability of database systems
Prof. Mozafari is passionate about building large-scale data-intensive systems that are more scalable, more robust, and more predictable.
Michael J. Cafarella selected for Sloan Research Fellowship
He has built software systems for information extraction, database integration, and feature engineering and applied these to problems in the social sciences.
Shadows in the Dark Web
Secrets lurk in the dark web, the 95 percent of the internet that most of us can’t see. One U-M professor is bringing some of those secrets to light, making the digital and the real world a little safer.

Kang G. Shin recognized with Distinguished Leadership Award by IEEE Computer Society Technical & Conference Activities Board
His work in the area of real-time computing has spanned decades and has had impact in a broad range of applications.

Prof. Danai Koutra recognized as rising star with ACM SIGKDD Award
The Rising Star Award is based on an individual’s whole body of work in the first five years after the PhD.

Parinaz Naghizadeh, Researcher in economic network security, is named a Barbour Scholar
Parinaz’s research is in combining communications with economics to assess the security of a network and then apply that to cyber-insurance contracts.

Yang Liu receives Best Applications Paper Award for cyber security research in phishing
His paper detailed his use of big data analysis to solve a major problem of cyber security.

Fighting cyber crime with data analytics
QuadMetrics offers a pair of services to help companies both assess the effectiveness of their security and decide the best way to allocate (or increase) their security budget.

U-M cyber security startup purchased by FICO
Analytic software company FICO of San Jose, Calif., bought QuadMetrics to help in its development of a FICO Enterprise Security Score.

The art of cyber war with Isaac Porche
Porche shares the global state of cyber warfare, and how his time at Michigan led him to the front lines.

Inaugural ECE Willie Hobbs Moore Alumni Lecture: Dr. Isaac R. Porche III
Porche discussed the changing definition of war and how information is playing a greater role than ever.

Data security for a safer world
ECE alum Kurt Rohloff helped create one of the world’s best homomorphic encryption software libraries, and he reflects on how his time at Michigan helped shape his career.

Advancing the future of circuit design with Intel’s Dr. Eric Karl
Karl (BSE MSE PhD EE) talks about how his time at Michigan helped prepare him for his dream job at Intel and a career advancing embedded memory technology and circuits.

The NAE invites Prof. Necmiye Ozay to symposium to advance the engineering frontier
Ozay presented on her research that is relevant to cybersecurity and the future of space exploration.

Mingyan Liu named Alice L. Hunt Collegiate Professor of Engineering
Mingyan Liu, renowned for her research specializing in communication networks and cybersecurity, has served as Chair of ECE since 2018. (video of the talk now available)

‘Perfect black’ coating can render a 3D object flat, raises intriguing dark veil possibility in astronomy
The carbon nanotube carpet is about half the thickness of a sheet of paper and absorbs 99.9 percent of the light that hits it.
James McCullagh receives Best Student Paper Award for research to keep bridges safe
McCullagh is working to develop energy harvesting devices and circuits to power wireless sensor nodes which can monitor bridge health.
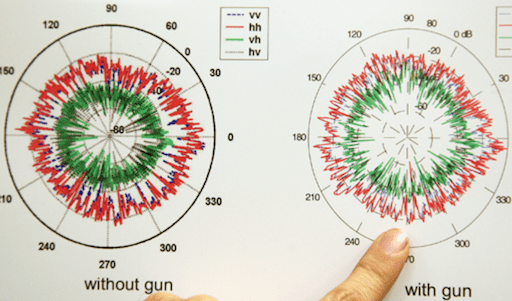
After Newtown: A new use for a weapons-detecting radar?
The technology could potentially identify a hidden weapon from a distance in less than a second.

New laser shows what substances are made of; could be new eyes for military
By shining the laser on a target and analyzing the reflected light, researchers can tell the chemical composition of the target.

When GPS fails, this speck of an electronic device could step in
The research group developed special fabrication processes that allows them to stack and bond seven different devices in layers.

Shrinking the size of optical systems, exponentially
The researchers believe that metasurfaces could one day be used to completely control the phase, amplitude, and polarization of light.
Prof. Pallab Bhattacharya to receive 2015 IEEE David Sarnoff Award
Since coming to the University in 1984, Bhattacharya has pioneered several important technological advances.

Prof. Becky Peterson awarded DARPA Young Faculty Award to investigate new materials for power semiconductor devices
Peterson’s findings could be used in wireless sensing and actuation systems, including those that deal with monitoring of the environment and medical conditions.

Prof. Kamal Sarabandi elected President of IEEE Geoscience and Remote Sensing Society
The IEEE Geoscience and Remote Sensing Society is a remote sensing organization with more than 3700 members around the globe.

Yelin Kim wins Best Student Paper Award at ACM Multimedia 2014 for research in facial emotion recognition
She computationally measures, represents, and analyzes human behavior data to illuminate fundamental human behavior and emotion perception, and develop natural human-machine interfaces.

Yi-Chin Wu receives ProQuest Distinguished Dissertation Award for research in network security
Her dissertation focused on “opacity,” which captures whether a given secret of the system can be inferred by intruders who observe the behavior of the system.

Thomas Chen earns NSF Graduate Research Fellowship for research in artificial neural networks for computer vision
Thomas and his group are working to improve upon artificial neural network design through a process called sparse coding.

Two Michigan papers win top awards at IEEE Security and Privacy Symposium
One of the paper describes and demonstrates a malicious hardware backdoor. The other demonstrated security failings in a commercial smart home platform.

Behzad Yektakhah earns paper award for research in seeing through walls
Yektakhah’s system improves on the speed, portability, and accuracy of many commercial models

Time-varying metamaterials for next generation communication, sensing, and defense systems
With $7.5M MURI grant, Professor Anthony Grbic is developing metamaterials for a new generation of integrated electromagnetic and photonic systems.

Xueru Zhang awarded Rackham Predoctoral Fellowship
Zhang is working to improve data security and address important ethical issues related to AI and discriminatory data sets.

First IFIP Workshop on Intelligent Vehicle Dependability and Security
The workshop, co-organized by a team including two EECS faculty, focused on ensuring the safety of Level 3 autonomous vehicles, where humans must be ready to take over control.

Embracing Risk: Cyber insurance as an incentive mechanism for cybersecurity
This new book by Mingyan Liu offers an engineering and strategic approach to improving cybersecurity through cyber insurance

Mingyan Liu: Confessions of a pseudo data scientist
Liu’s most recent research involves online learning, modeling of large-scale internet measurement data, and incentive mechanisms for security games.

Mingyan Liu, 2018 Distinguished University Innovator, talks about her company and data science commercialization
Mingyan Liu, recipient of the 2018 Distinguished Innovator of the Year award, gave a talk about her startup company and participated on a panel discussing data science commercialiation.
Michigan startup MemryX, Inc. promises faster, cheaper AI processing
The ECE startup builds neuromorphic computer chips uniquely suitable for AI applications
The post Michigan startup MemryX, Inc. promises faster, cheaper AI processing appeared first on Michigan Engineering News.
Egg-carton-style patterning keeps charged nanoparticles in place and suitable for a wide range of applications
Prof. Jay Guo and his team discovered a scalable way to settle down and precisely arrange micro- and nano-sized particles according to size
The post Egg-carton-style patterning keeps charged nanoparticles in place and suitable for a wide range of applications appeared first on Michigan Engineering News.
$7.75M for mapping circuits in the brain
A new NSF Tech Hub will put tools to rapidly advance our understanding of the brain into the hands of neuroscientists.
The post $7.75M for mapping circuits in the brain appeared first on Michigan Engineering News.
A 3D camera for safer autonomy and advanced biomedical imaging
Researchers demonstrated the use of stacked, transparent graphene photodetectors combined with image processing algorithms to produce 3D images and range detection.
The post A 3D camera for safer autonomy and advanced biomedical imaging appeared first on Michigan Engineering News.
Nanotech OLED electrode liberates 20% more light, could slash display power consumption
A five-nanometer-thick layer of silver and copper outperforms conventional indium tin oxide without adding cost.
The post Nanotech OLED electrode liberates 20% more light, could slash display power consumption appeared first on Michigan Engineering News.
Hacking into homes: Security flaws found in SmartThings connected home system
New vulnerabilities form when hardware like electronic locks, thermostats, ovens, sprinklers, lights and motion sensors are networked and set up to be controlled remotely.
Internet-scanning U-M startup offers new approach to cybersecurity
Censys is the first commercially available internet-wide scanning tool. It helps IT experts to secure large networks with a constantly changing array of devices.
The post Internet-scanning U-M startup offers new approach to cybersecurity appeared first on Michigan Engineering News.
Cuba ‘sonic attacks’: A covert accident?
‘We’ve demonstrated a scenario in which the harm might have been unintentional.’
The post Cuba ‘sonic attacks’: A covert accident? appeared first on Michigan Engineering News.
CSE PhD student Matt Bernhard on the Facebook data breach
In this video, CSE PhD Student Matt Bernhard weighs in on the matter Facebook data harvesting, such as that done by Cambridge Analytica.
The post CSE PhD student Matt Bernhard on the Facebook data breach appeared first on Michigan Engineering News.
‘I hacked an election. So can the Russians.’
Professor Alex Halderman and the New York Times staged a mock election to demonstrate voting machine vulnerability.
The post ‘I hacked an election. So can the Russians.’ appeared first on Michigan Engineering News.
Zuckerberg Capitol Hill testimony: Engineering experts offer comments
U-M profs weigh new business model, European-style regulation
The post Zuckerberg Capitol Hill testimony: Engineering experts offer comments appeared first on Michigan Engineering News.
Intel processor vulnerability could put millions of PCs at risk
Patches can provide protection.
The post Intel processor vulnerability could put millions of PCs at risk appeared first on Michigan Engineering News.
Not enough voters detecting ballot errors and potential hacks, study finds
Researchers carried out the first study on voter behavior with electronic assistive devices, found 93% missed incorrect ballots.
The post Not enough voters detecting ballot errors and potential hacks, study finds appeared first on Michigan Engineering News.
New remote voting risks and solutions identified
The upcoming presidential election in the middle of a pandemic has many jurisdictions exploring new technologies. They’re not secure.
The post New remote voting risks and solutions identified appeared first on Michigan Engineering News.
5 ways Americans can keep their vote secure and accurate
Expert advice for voting in an unprecedented election.
The post 5 ways Americans can keep their vote secure and accurate appeared first on Michigan Engineering News.

An even smaller world’s smallest ‘computer’
The latest from IBM and now the University of Michigan is redefining what counts as a computer at the microscale.
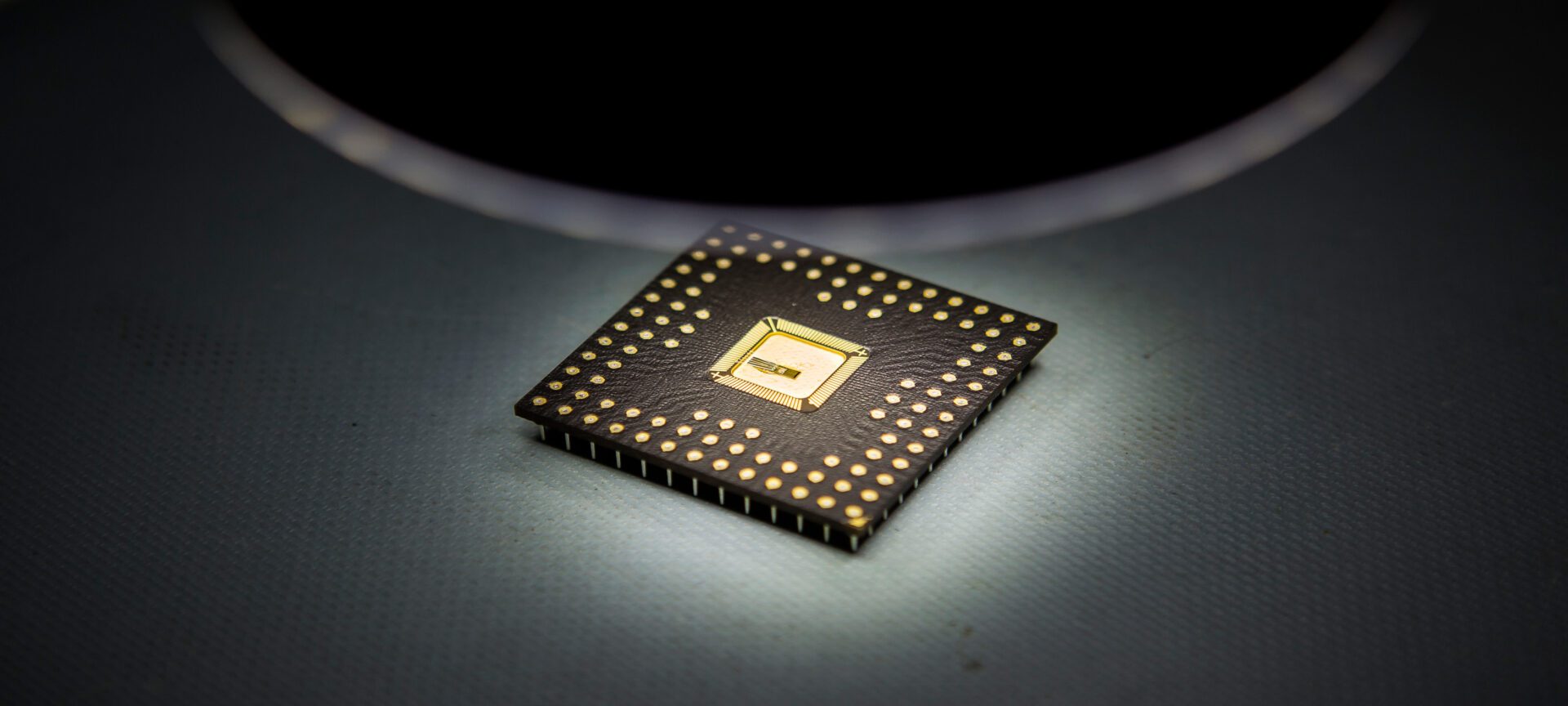
Beyond Moore’s law: $16.7M for advanced computing projects
DARPA’s initiative to reinvigorate the microelectronics industry draws deeply on Michigan Engineering expertise.
How Let’s Encrypt doubled the percentage of secure websites in four years
A Q&A with J. Alex Halderman, who co-founded the nonprofit organization.
The post How Let’s Encrypt doubled the percentage of secure websites in four years appeared first on Michigan Engineering News.
$1.8M DARPA project aims to protect cars, trucks and spacecraft from hackers
Ironpatch could head off growing danger of security vulnerabilities in vehicle systems.
The post $1.8M DARPA project aims to protect cars, trucks and spacecraft from hackers appeared first on Michigan Engineering News.
A breakthrough for large scale computing
New software finally makes ‘memory disaggregation’ practical.
The post A breakthrough for large scale computing appeared first on Michigan Engineering News.

Big data, small footprint
How changing the rules of computing could lighten Big Data’s impact on the internet.
Election lessons from Michigan
Election security expert J. Alex Halderman dissects Antrim County’s election debacle to help future contests go more smoothly.
The post Election lessons from Michigan appeared first on Michigan Engineering News.
Less nosy smart speakers
Technology could capture household information without recording speech.
The post Less nosy smart speakers appeared first on Michigan Engineering News.
Her fight for your rights
Could censorship end the internet as we know it? Not if Roya Ensafi can help it.
The post Her fight for your rights appeared first on Michigan Engineering News.
In the news: Michigan Engineering experts August 2-6
Highlights include Wired and CNN.
The post In the news: Michigan Engineering experts August 2-6 appeared first on Michigan Engineering News.
Will power cords go the way of land lines?
Room-size charging system powers lights, phones, laptops without wires
The post Will power cords go the way of land lines? appeared first on Michigan Engineering News.
Wireless electricity and safety: A Q&A with Alanson Sample
How the safety of a wireless charging room stacks up to that of a cell phone.
The post Wireless electricity and safety: A Q&A with Alanson Sample appeared first on Michigan Engineering News.
Batteryless next-generation cellular devices could empower a more sustainable future
PhD student Trevor Odelberg is looking to enable long range, highly reliable, and low-power cellular IoT devices that one day can run entirely on harvested energy, reducing battery waste and empowering devices to last for decades.
The post Batteryless next-generation cellular devices could empower a more sustainable future appeared first on Michigan Engineering News.
$6.25 million to develop new semiconductors for artificial photosynthesis
An interdisciplinary team from four universities are developing a new class of semiconductors for novel artificial photosynthesis and the production of clean chemicals and fuels using sunlight, as part of a DoD MURI
The post $6.25 million to develop new semiconductors for artificial photosynthesis appeared first on Michigan Engineering News.
“Egg carton” quantum dot array could lead to ultralow power devices
By putting a twist on new “2D” semiconductors, researchers have demonstrated their potential for using single photons to transmit information.
The post “Egg carton” quantum dot array could lead to ultralow power devices appeared first on Michigan Engineering News.

Computer vision: Finding the best teaching frame in a video for fake video fightback
The frame in which a human marks out the boundaries of an object makes a huge difference in how well AI software can identify that object through the rest of the video.
Autonomous vehicles can be fooled to ‘see’ nonexistent obstacles
Vehicles that perceive obstacles that aren’t really there could cause traffic accidents.
The post Autonomous vehicles can be fooled to ‘see’ nonexistent obstacles appeared first on Michigan Engineering News.
A shoe-box-sized chemical detector
Powered by a broadband infrared laser, the device can zero in on the ‘spectral fingerprint region’.

How predictive modeling could help us reopen more safely
Graphical online simulation could spur more targeted COVID-19 protection measures.
Pioneering a way to keep very small satellites in orbit
More than 250 students had a hand in a satellite scheduled to launch on January 17th, the first in space for a project to keep nanosats in orbit by harnessing Earth’s magnetic field.
The post Pioneering a way to keep very small satellites in orbit appeared first on Michigan Engineering News.
DARPA pitted 500+ hackers against this computer chip. The chip won.
University of Michigan’s MORPHEUS technology emerges unscathed from bug bounty effort.
The post DARPA pitted 500+ hackers against this computer chip. The chip won. appeared first on Michigan Engineering News.
In the news: Michigan Engineering experts June 14-18
Highlights include Popular Science, CNet and Science Alert
The post In the news: Michigan Engineering experts June 14-18 appeared first on Michigan Engineering News.
In the news: Michigan Engineering experts July 19-23
Highlights include the CBC and MLive.
The post In the news: Michigan Engineering experts July 19-23 appeared first on Michigan Engineering News.
In the news: Michigan Engineering experts May 10-14
Highlights include The Conversation, MLive and the Washington Post.
The post In the news: Michigan Engineering experts May 10-14 appeared first on Michigan Engineering News.
In the news: Michigan Engineering experts May 17-21
Highlights include NPR, Popular Science and The Conversation.
The post In the news: Michigan Engineering experts May 17-21 appeared first on Michigan Engineering News.
In the news: Michigan Engineering experts August 9-13
Highlights include the Los Angeles Times.
The post In the news: Michigan Engineering experts August 9-13 appeared first on Michigan Engineering News.
In the news: Michigan Engineering experts September 27 – October 1
Highlights include Nature and Newsweek.
The post In the news: Michigan Engineering experts September 27 – October 1 appeared first on Michigan Engineering News.
In the news: Michigan Engineering experts June 7-11
Highlights include Newsweek and The Conversation.
The post In the news: Michigan Engineering experts June 7-11 appeared first on Michigan Engineering News.

Catching nuclear smugglers: fast algorithm could enable cost-effective detectors at borders
The algorithm can pick out weak signals from nuclear weapons materials, hidden in ordinary radiation sources like fertilizer.
In the news: Michigan Engineering experts May 24-28
Highlights include Bloomberg, New York Times and the Detroit News.
The post In the news: Michigan Engineering experts May 24-28 appeared first on Michigan Engineering News.
“Learning database” speeds queries from hours to seconds
Verdict can make databases deliver answers more than 200 times faster while maintaining 99 percent accuracy.
The post “Learning database” speeds queries from hours to seconds appeared first on Michigan Engineering News.
Chat tool simplifies tricky online privacy policies
Register for an account on just about any website or download an app to your smartphone and you likely will encounter that pesky, “I certify that I’ve read and understand the privacy policy,” check box. “Typically drafted by lawyers, these documents tell you, ‘This the information we’re collecting, this is how we’re processing it, this […]
The post Chat tool simplifies tricky online privacy policies appeared first on Michigan Engineering News.
Fake news detector algorithm works better than a human
System sniffs out fakes up to 76 percent of the time.
The post Fake news detector algorithm works better than a human appeared first on Michigan Engineering News.
Detecting Huntington’s disease with an algorithm that analyzes speech
New, preliminary research found automated speech test accurately diagnoses Huntington’s disease 81 percent of the time and tracks the disease’s progression.
The post Detecting Huntington’s disease with an algorithm that analyzes speech appeared first on Michigan Engineering News.
Online censorship detector aims to make the internet a freer place
Censored Planet could provide new insight into the flow of online information
The post Online censorship detector aims to make the internet a freer place appeared first on Michigan Engineering News.
First programmable memristor computer aims to bring AI processing down from the cloud
Circuit elements that store information in their electrical resistances enable a brain-like form of computing, storing and processing information in the same place.
The post First programmable memristor computer aims to bring AI processing down from the cloud appeared first on Michigan Engineering News.
How Russia’s online censorship could jeopardize internet freedom worldwide
The nation is using inexpensive commodity equipment to block 170K domains on more than 1K privately-owned ISPs.
The post How Russia’s online censorship could jeopardize internet freedom worldwide appeared first on Michigan Engineering News.
$20M NSF AI-EDGE Institute aims to transform 5G and beyond networks
U-M is a core member of a new NSF-led Institute that is a collaboration between 11 institutions, three government research labs, and four global companies.
The post $20M NSF AI-EDGE Institute aims to transform 5G and beyond networks appeared first on Michigan Engineering News.
Hunger and COVID: Fighting pandemic-related food insecurity in Detroit
Public policy and engineering team up to improve food access.
The post Hunger and COVID: Fighting pandemic-related food insecurity in Detroit appeared first on Michigan Engineering News.
Wireless sensors for N95 masks could enable easier, more accurate decontamination
“The technology can give users the confidence they deserve when reusing respirators or other PPE.”
The post Wireless sensors for N95 masks could enable easier, more accurate decontamination appeared first on Michigan Engineering News.
Powering robots: biomorphic batteries could provide 72 times more energy than stand-alone cells
The researchers compare them to fat deposits in living creatures.
The post Powering robots: biomorphic batteries could provide 72 times more energy than stand-alone cells appeared first on Michigan Engineering News.
Distributed protocol underpinning cloud computing automatically determined safe and secure
Two researchers have debunked the common assumption that the famous Paxos consensus protocol is too complex to be proven safe without hours of manual labor.
The post Distributed protocol underpinning cloud computing automatically determined safe and secure appeared first on Michigan Engineering News.
5 ways to keep vaccine cold storage equipment safe from hackers
A medical security expert outlines the risks and how hospitals can protect themselves.
The post 5 ways to keep vaccine cold storage equipment safe from hackers appeared first on Michigan Engineering News.
‘Exciton surfing’ could enable next-gen energy, computing and communications tech
A charge-neutral information carrier could cut energy waste from computing, now that it can potentially be transported within chips.
The post ‘Exciton surfing’ could enable next-gen energy, computing and communications tech appeared first on Michigan Engineering News.

Immune to hacks: Inoculating deep neural networks to thwart attacks
The adaptive immune system serves as a template for defending neural nets from confusion-sowing attacks
Open source platform enables research on privacy-preserving machine learning
Virtual assortment of user devices provides a realistic training environment for distributed machine learning, protects privacy by learning where data lives.
The post Open source platform enables research on privacy-preserving machine learning appeared first on Michigan Engineering News.
Next generation neural probe leads to expanded understanding of the brain
The hectoSTAR probe, with 128 stimulating micro-LEDs and 256 recording electrodes integrated in the same neural probe, was designed for some stellar brain mapping projects
The post Next generation neural probe leads to expanded understanding of the brain appeared first on Michigan Engineering News.
Photosynthesis copycat may improve solar cells
The new approach moves energy efficiently and could reduce energy losses converting light into electricity.
The post Photosynthesis copycat may improve solar cells appeared first on Michigan Engineering News.
Breakthrough in green micro-LEDs for augmented/mixed reality devices
Prof. Zetian Mi’s team are the first to achieve high-performance, highly stable green micro-LEDs with dimensions less than 1 micrometer on silicon, which can support ultrahigh-resolution full-color displays and other applications.
The post Breakthrough in green micro-LEDs for augmented/mixed reality devices appeared first on Michigan Engineering News.
 Michigan Engineering | University of Michigan
Michigan Engineering | University of Michigan