Thomas and his group are working to improve upon artificial neural network design through a process called sparse coding.
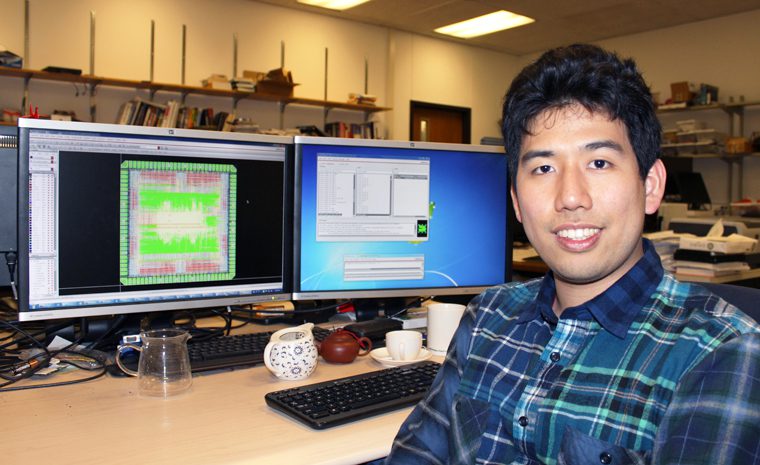

Thomas and his group are working to improve upon artificial neural network design through a process called sparse coding.
The U-M Board of Regents approved the College of Engineering’s new robotics building project on April 16. The three-story, 100,000-square-foot facility is slated for Hayward Street just east of the Space Research Building on North Campus.
The post High-tech robotics center coming to U-Michigan appeared first on Michigan Engineering News.
A really big chip is ready to take on really big challenges.

Prof. Forrest is widely acknowledged as one of the most successful academic inventors and entrepreneurs today.
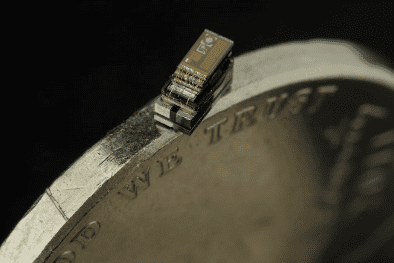
A brief history of what led to the technical feat known as the Michigan Micro Mote, a tiny speck of a computer that does it all.

Her dissertation focused on “opacity,” which captures whether a given secret of the system can be inferred by intruders who observe the behavior of the system.
HiJack is a hardware/software platform that utilizes the headset jack on a smartphone as a universal power/data interface.
The son of Hungarian Holocaust survivors, Tamas Gombosi took an unlikely path to his post as an eminent space scientist at U-M.
The post Lecture offers a planetary scientist’s tour through the solar system appeared first on Michigan Engineering News.

How and why we make machines that move like us.
The post In our image appeared first on Engineering Research News.

The SMAP mission is NASA’s most ambitious sensing project yet for measuring global soil moisture levels.